Since the summer of 2008 there are offline devices for the access system. This devices can be operated with each FHGR-Card.
The system includes the following components:
Offline-System
The system works without a physical connection between the cylinder lock and the access system.
Each FHGR-Card contains two data records for the access:
All the rights for a FHGR-Card are stored on the card. For a change of these rights it is necessary to update the card on an update terminal.
For security reasons the rights are only valid for a limited timeperiod which is stored on the timestamp. Actually this timeperiod is set to 7 days. After this period the rights are useless and the card shoud be updatet on a terminal. The timestamp can be updated at an update terminal or at a special configured online reader.
The FH Graubünden has implemented an access system, which works with the FHGR-Cards.
Online-Systems
The online devices are connected to the system and query the access permition in realtime. An access which is connected to the system has to be connected to the network and to the current. Entrees to the offices as well as to leased rooms are equipped with offline systems.
Following doors are connected to the online access system:
- All main entrances (incl. entrances Zurich)
- Car park entrance, Pulvermühlestrasse 57
- Elevators, Pulvermühlestrasse 57
The notebook-shelves for the students are online too.
To set up an Exchange account the following settings are required:
To get access to the University of Applied Sciences of the Grisons VPN with your Andorid smartphone, you have to do the following steps:
Detailed instructions can be found in the appendix.
MFA / 2FA authentication is now required.
For the use of the protected FH Graubünden WLAN with an "Android" operating system, the following settings on the device are required:
Detailed instructions can be found in the appendix
It is no longer possible to order Adobe licenses via Studyhouse/Asknet. A successor solution will be provided and communicated by the start of the fall semester at the latest.
Important: If you would like to continue to benefit from low-cost licensing via the University of Applied Sciences of the Grisons, do not renew your licenses via other channels (e.g. directly with Adobe), as these can usually have more expensive monthly prices.
Citavi is a reference management software, which you can get over the FH Grisons.
If you have any questions you can write an E-Mail to the following Mail-Address: citavi@fhgr.ch
The link to the Download of Citavi, as well as an introduction, can be found in the appendix.
Cubus Dienst
Wenn das Cubus Programm keine Lizenz mehr finden kann, kann man diese Datei im Link unten herunterladen und die Reparatur ausführen.
Cubus Dienst Reparaturprogramm
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010024
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010026
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010028
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010030
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010029
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010031
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010032
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010033
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010034
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010035
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010036
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010037
The software supports structural engineers in efficiently calculating the load-bearing capacity and stability of building structures in building and foundation engineering.
The installation file and instructions (only in German) can be found in the appendix.
Finden Sie Informationen zum Drucken und Scannen an der FH Graubünden ab 12.08.2024 auf der neuen Wissensplattform.
The FH Graubünden offers its users the opportunity to use the WLAN "eduroam".
Eduroam is the international roaming-platform for universities and research institutions with more than 7000 access points worldwide.
Once the WLAN “eduroam” is set up, the user can connect with his FH Graubünden-account to the eduroam-network and to the Internet for free – without any adjustments.
If you want to log in with a FH Graubünden-account in this Network, you have to add "@fhgr.ch" after your username.
Instructions for different platforms can be found on the Intranet, where the other instructions are or below this article in "Other topics that might interest you".
All fixed and variable employees receive a personal identification card.
This card combines the following functions:
- Employee Identification
- Free copy card
- Cashless payment at the cafeteria and vending machines (Cafeteria-account)
- Access authorisation and liftaccess
Cafeteria
The employee identification card has a separate account for the cafeteria. On this account you can charge money regardless of the copy-account. With this money you can pay at the cafeteria.
You can charge the money on a charging station of the FH Graubünden.
Access systems
The FHGR-Card is used as a key with which you can access the offices such as the elevatores of the FH Graubünden.
Not fixed or variable employees can purchase a Cash-Card at the administration for a depot of Fr 20 -.
The Cash-Card combines the following functions:
- Copycard (Copy-account)
- Cashless payment at the cafeteria and vending machines (Cafeteria-account)
Copy
On every Cash-Card there is a Copy-account on which you can charge money to copy.
The printouts will be charged according to the current price list of the FH Graubünden.
You can charge the money on a charging station of the FH Graubünden .
Cafeteria
The Impersonal Cash-Card contains a separate account for the cafeteria.
On this account you can charge money regardless of the copy-account. With this money you can pay at the cafeteria.
You can charge the money on a charging station of the FH Graubünden.
All enrolled students at the FH Graubünden get a personal student identification card.
The Student Identification Card combines the following functions:
- LEGI (student identification/student card)
- Copy-/Printcard
- Cashless payment at the cafeteria and vending machines (Cafeteria-account)
- Access authorisation and liftaccess (only on request)
- different benefits
Cafeteria
The Student Identification Card has a separate account for the cafeteria. On this account you can charge money. With this money you can pay at the cafeteria.
You can charge the money on a charging station of the FH Graubünden.
Access systems
In given cases the Student Identification Card can be used as a key for example for the lifts of the FH Graubünden.
Students / Employees
For each student/employee the first FHGR-Card is for free.
Students/employees have to pay SFr. 20.- for the replacement of a lost or damaged card. The charged amounts will be repaid whenever possible.
Cash-Card
For lost or defect Cash-Cards the SFr. 20.- depot will be retained. For a new card you have to pay a new depot of SFr. 20.-. The charged amounts will be repaid whenever possible.
New card order
New cards can be orderd over the contact form.
For the balance of lost or damaged cards, the FH Graubünden can not be held liable.
For the delivery of large amount of data (until 300 Gigabyte) the Switch Filesender can be used. That's useful for a single delivery of a large amount of data. This is possible from you to your associate, or on invitation to you or to a third person from your associate.
To find out the installed MAC version you have to click on the apple and then on „about this Mac“.
A window with the MAC version appears.
To use the programm, do as follwed:
AIMMS is a prescriptive analytics tool for mathematical modelling, optimization and simulation. To use the software with an academic license, proceed as follows:
The McAfee antivirus software is free available for all students and employees of the FH Graubünden.
Windows
Mac
Detailed instructions and a link to the downloads can be found in the appendix.
The statics and structural design of 2D bar structures software RuckZuck is avaible for all employees and students of the FHGR:
Detailed instructions can be found in the appendix.
To get access to the FHGR VPN with your iPhone, you have to do the following steps:
Detailed instructions can be found in the appendix.
MFA / 2FA authentication is now required.
For the use of the protected FH Graubünden WLAN with an iPhone, the following settings are required:
Detailed instructions can be found in the appendix.
The instruction document of LimeSurvey can be found in the appendix.
Topics in the instruction document:
- Basics LimeSurvey
- Create a survey
To activate a survey for other persons (group work, etc.), all persons must have registered once in the Limesurvey.
The survey-ID and the persons to be released must be reported to the support (support@fhgr.ch).
The LinkedIn Learning website provides access to over 8,000 exercise videos and over 300,000 video tutorials covering development, design, web, photography, business, education, 3D animation, video, and audio + music.
Instructions on how to log in to LinkedIn works can be found in the appendix.
To charge money on your FHGR-Card you have to go to a charging station. The various charging stations can be found at the following locations:
Building A; Pulvermühlestrasse 57, in front of toilet entrance
Building B; Ringstrasse 34, 3. OG
Building C; Pulvermühlestrasse 80
Building E; Comercialstrasse 22, at the library next to the exit to the cafeteria
Building H; Comercialstrasse 19, 1. OG next to the administration
Building I; Sommeraustrasse, Copy-room
Building Z; Limmatstrasse, Lounge in the basement
Update terminals


The update terminals can be found at the following locations:
- Building A, EG, on the left side of the charging station across the toilets
- Building B, 2. OG, on the left side of the entry
- Building D, 1. OG, on the left side of the entry
- Building F, EG, on the left side of the entry to the Student Services
- Building H, 1. OG, on the left side of the entry
- Building I, in the copyroom on the left side of the door
Online reader (card reader)

Also some online reader are equipped for the update of the timestamp:
- Building A, 1. OG, first reader of the notebook locker (Shelf Nr. 250)
- Building B, 1. OG, entry to the telecom laboratory
- Building F, 1. OG, first reader of the notebook locker (Shelf Nr. 1139)
Attention: Should the online reader flash alternately blink red and green is an update of the rights at an update terminal necessary.
The update starts automatically when the card is placed on an update terminal/online reader and usually lasts a few seconds.
The access to eduroam WLAN at the FH Graubünden is also possible for MAC OS . All actual versions of OS X are similar.
Detailed instructions can be found in the appendix.
It is possible to use the VPN-Client of the FHGR Chur with the Mac OS X:
Detailed instructions can be found in the appendix.
To use the FH Graubünden Exchange account with the iPhone, you have to make the following settings:
The instruction document of Mail-Archiving can be found in the appendix.
Topics in the instruction document:
- Basics archiving
- Use of the archiving in Outlook
- Use of the archiving in Webmail
Notice: The instruction document is only available in German.
All bachelor and master students (further education excluded) get a mailadress from the FH Graubünden.
The username is the same as the one works with the other systems on the FH Graubünden. The password is the same for the first time. The password for the mailbox can be changed independently of other systems.
All guidance in dealing with this email address can be taken directly on the site of our partner Exigo.
You need an active connection with the VPN client (Pulse Secure) from the FH Graubünden in order to use MAXQDA.
Mendeley is a reference management software, which you can get for free from the producer website.
If you have any questions you can write an E-Mail to the following Mail-Address: citavi@fhgr.ch
The link to the Download of Mendeley, as well as an introduction in German, can be found in the appendix.
Setting up OneDrive for lecturers and students
Registration is via Microsoft Login. Please use your Univerity of Applied Sciences of the Grisons account to register. OneDrive can only be used online or additionally set up locally on the PC. The local installation takes place together with the Office applications, further information can be found in the corresponding support site (Office 365).
The setup for employees with a notebook of the University of Applied Sciences of the Grisons is done by the IT department.
Multiple OneDrive accounts
Several OneDrive accounts can be used in parallel, for example you can use OneDrive from the University of Applied Sciences of the Grisons in parallel with a private OneDrive account. To add more accounts, right-click the OneDrive icon in the taskbar. Under "Settings" select the "Account" tab and click on "Add account".
Restore deleted files and folders in OneDrive
Microsoft's support page has instructions how to restore accidentally deleted data. Please note that items in the recycle bin are automatically deleted after 93 days. After this period or if you delete files or folders from the recycle bin yourself, there is no way for students to restore the data. For employees with a notebook of the University of Applied Sciences of the Grisons, an additional backup will be created by the IT department.
Location for OneNote
If OneDrive is set up, it will be used as the default OneNote save location. The default storage location can be adjusted under "File", "Options", "Settings", "Properties", "Save & Backup". Changing the storage location of an individual notebook is possible under «File», «Settings», «Properties», «Change storage location...».
Procedure when leaving the University of Applied Sciences of the Grisons
The validity of the Microsoft license expires when you leave the University of Applied Sciences of the Grisons. It is therefore important that you back up your data before you leave and save it on a private medium. For example locally on the PC, on a USB stick, on an external hard drive or in another cloud. This applies to data from the University of Applied Sciences of the Grisons OneDrive, in OneNote, Teams or Moodle.
I got my license from SoftwareONE
If you obtained your license through SoftwareONE, you can continue to use it until it expires. You can then obtain a new license (free of charge) from Microsoft. Use your University of Applied Sciences of the Grisons account to register.
Important: you are responsible for migrating your data yourself, this does not happen automatically.
The instruction document for using OneDrive for employees can be found in the appendix.
Notice: The instruction document is only available in German.
Multi-factor authentication (MFA) is being gradually introduced at FHGR.
Registration of additional authentication methods is possible at any time.
Registration MFA at Microsoft
1. Call up the registration link aka.ms/MFASetup
2. Select and configure MFA method.
The following additional authentication methods are available:
Authentication phone (SMS code or callback)
After entering the phone number, you can choose how the contact should take place. Either a code is sent via SMS or a callback must be made.
Telephone (business)
For employees with a registered telephone number, this is already pre-filled. A telephone call is made.
Mobile app
For the mobile app, either the Microsoft Authenticator app or a third-party app can be used (e.g. Google Authenticator app, andOTP, etc.).
Notification (push notification in the app)
This variant only works with the Microsoft Authenticator app.
Select the option “Receive notifications for verification” and then “Set up”. Scan the QR code with the Microsoft Authenticator app.
Use verification code (Microsoft Authenticator app)
Select the option “Use verification code” and then “Setup”. Scan the QR code with the Microsoft Authenticator app.
Use verification code (third-party app)
Select the option “Use verification code” and then “Setup”. Click "Configure app without notifications" next to the QR code and scan the QR code with the third-party app.
Schedule and services with MFA
VPN: MFA in operation
Q2 2024: Webmail Exchange (employees) and Office 365
Q3 2024: More services by priority
Diese Information wurde bereits auf die neue Wissensplattform übertragen, lesen Sie sie da:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010060
This information should help you, buying a new notebook. Below is a list of some suppliers for students (of course there are other suppliers, so compare the prices).
Recommended minimum requirements
Notes to MAC-Systems
Notes for MMP-Major
• own Headset (headset with Mic)
• own Microfon for Smartphone/HD-Camera
As a student or employee of the FHGR, Microsoft software products can be obtained at reduced prices, and under certain circumstances even free of charge.
Employee
All software products for work purposes are procured, managed and installed centrally via the IT service. Contact support directly. For private purposes, the Microsoft Office package can be obtained free of charge from Microsoft Online. Use your FH Graubünden account to register.
Students
The Microsoft Office package (Outlook, Word, PowerPoint, Excel and OneNote) can be obtained free of charge from Microsoft Online. Use your FH Graubünden account to register.
The local installation can be called up using the "Install Office" button in the top right corner. With the student license you can also use Office online. OneNote can be connected to OneDrive or alternatively to a Switchdrive account.
Microsoft Azure Development Tools for Academic Purposes:
Microsoft provides various software and operating systems for teaching. This includes MS Visio, MS Access and current Windows operating system versions.
The instruction document of OneNote 2016 can be found in the appendix.
Notice: The instruction document is only available in German.
It is desirable that employees of the FH Graubünden hold their Outlook calendar up to date and share it to the other employees.
To share your calendar to all employees you have to do the following steps:
More specific instructions can be found in the appendix.
To configure the E-Mail account of the HTW-Chur in Outlook use the manuel in the appendix.
Attention: If the plotting-system with Mac OS X 10.10 Yosemite shouldn't work, you have to do the configuration steps at the beginning of the introduction in the appendix.
It is possible to use the plotting-system with MAC OS X Lion, Mountain Lion, Mavericks, Yosemite, El Capitan, Sierra, High Sierra or Mojave.
For a quick install of the Plotter, we've provided a script used in the terminal. You can execute it, as followed described:
Detailed instructions without the script, can be found in the appendix.
For printig with Android devices at the FH Graubünden you can use the Everyone-Print solution. There are two options:
or
You can ignore messages like "gethistoryprintjobsforusername". The second option is explained in detail in the document below.
At both options the document appears at the multifunction printers (Kopierer) at the FH Graubünden in the printing-list of the Follow-You-Prints and will be charged according to the price list of the FH Graubünden.
At the FH Graubünden the printing with IOS devices is possible with the Everyone-Print solution. There are two options:
or
The second option is explained in detail in the document below.
In both options the document appears on a multifunctional printer (Kopierer) of the FH Graubünden in the document list of the Follow-You-Prints and will be charged according to the price list of the FH Graubünden.
Attention: If the printing with Mac OS X 10.10 Yosemite shouldn't work, you have to do the configuration steps at the beginning of the introduction in the appendix.
Attention: all Mac-Models with the M1 Chip must install an additional programm called "Rosetta". To find out if you have a Mac-Model with an M1 Chip go to the apple-icon on the upper left and go to "About this mac".
It is possible to use the printing-system with MacOS Sonoma and previous versions.
For a quick install of the Kopierer, we've provided a script used in the terminal. You can execute it, as followed described:
Detailed instructions without the script, can be found in the appendix.
The printing with mobile devices, which don't have IOS or Android as operating system, is possible through the EveryonePrint solution.
At the first time you use the Mail-printing you get a Feedback-mail for the registration of your mailadress in the system. It doesn't matter if you register with your FH Graubünden-mailaddress or not.
The document appears at the multifunction printers (Kopierer) at the FH Graubünden in the printing-list of the Follow-You-Prints and will be charged according to the price list of the FH Graubünden.
Most of the PC's at the FH Graubünden have a Shortcut on the Desktop with the Name "Printserver". With this shortcut you can open the list with all printers available at the FH Graubünden. With a doubleclick you can set up the desired printers.
Detailed instructions can be found in the appendix.
It is possible to use the printing-system over WLAN with all versions of Windows.
For more printers do the steps 1, 2 and 6 again.
Detailed instructions can be found in the appendix.
The entire campus of the FH Graubünden is covered with a non-encrypted wireless LAN. With a username and password of the FH Graubünden almost all wireless-enabled devices get access to the Internet.
The connection to the Internet is activated as long as your device is turned on. After restart, you will automatically be prompted to retype your information.
Detailed instructions for various devices can be found in the appendix.
The WLAN "public" also can be used without a HTW account:
Detailed instructions can be found in the appendix.
Diese Information wurde bereits auf die neue Wissensplattform übertragen, lesen Sie sie da:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010061
Meeting rooms of the FH Graubünden can be booked in Outlook by every employee.
Detailed instructions can be found in the appendix.
This information has already been transferred to the new knowledge platform, read it there:
https://fhgr.service-now.com/esc?id=kb_article&sysparm_article=KB0010039
Installation:
- Staff: Start the installation in the Softwarecenter
- Students: Use the introduction (only in German)
If you are outside of the FH Graubünden you need an activ connection with the VPN client (Pulse Secure) from the FH Graubünden.
The instruction document of SPSS can be found in the appendix.
Topics in the instruction document:
- spss_anwendung_neu_01: Basic knowledge, procedure and examples
- spss_it_01: Requirements, licenses, installation and access
- spss_anwendung_vertiefung_neu: Procedure and examples
Notice: The instruction document is only available in German.
SWITCHdrive offers the members of the FH Graubünden a secure alternative to comercial Cloud-Storage-Services (e.g. Dropbox). With SWITCHdrive files can be safed, synchronized, shared with others or edited together. There are 100GB storage space available for each user.
For the first use of SWITCHdrive an account has to be activated. An introduction you find in the appendix.
To set up a call forwarding you have to do the following steps:
Now on the display you can see, that your telephone is forwarded.
To deactivate the call forwarding you have to click the button "Rufuml. aus" again.
To use the Webinterface you have to open the following link:
https://cucmsrv01.fhgr.ch/ucmuser/
Enter your username and password in the login window.
Hint: The username ans password are the same as your FHGR username and password.
An introduction to the Webinterface can be found in the appendix.
Topics in the introduction:
- Basics Webinterface
- Use of Webinterface
Outside the University of Applied Sciences of the Grisons , an active VPN connection is required to access the webinterface.
A short instruction and detailed instructions of the distributor for our VoIP-devices can be found in the appendix.
In the detailed instructions you can find the following topics:
- Accept
- Hold/Pick up
- Switch between calls
- Hand over calls
- Conference
- Call forward
- Hunt
- Missed calls
- Voicemail
- Settings (e.g. ringtone)
- Telephone directory
Note: The instructions are only available in German.
The FH Graubünden can use the plagiarismdetection software Turnitin.
In case of suspicion, papers can be tested. Each course studies has key-users who are responsible for testing the papers. New users have to be applied by the IT Support (support@fhgr.ch).
The papers will be compared with the internet and papers already examined by the FH Graubünden.
The instruction document of the Voicemail can be found in the appendix.
Topics in the instruction document:
- Basics Voicemail
- Use of Voicemail
Notice: The instruction document is only available in German.
Die FH Graubünden stellt allen Benutzern (mit einem Account) einen Zugang zur Videokonferenzlösung von Cisco (Webex) zur Verfügung.
Webex Mitarbeiter
Bei Mitarbeitenden, welche ein Notebook der FH Graubünden besitzen (Windows) sind die Webex Tools bereits vorinstalliert und konfiguriert.
Anleitung für die Benutzung finden sie unten.
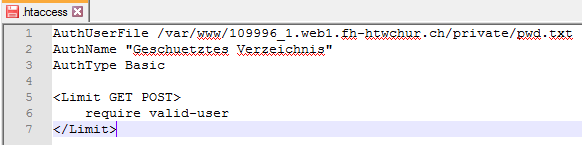
To password protect a directory on a web server, do the following:
The instruction document of Windows 10 can be found in the appendix.
With the VPN-access it is possible to work from home, or on the road, as if you were in the FHGR. Certain services will require this connection.
E.g SPSS or MAXQDA
At the first time you connect with the VPN, you have to install a small tool. Let the Internet Explorer install the appropriate ActiveX. For any further logins this step is unnecessary.
Detailed instructions with pictures can be found in the appendix.
MFA / 2FA authentication is now required.
The Microsoft OS supports the encryption for the eduroam.
Detailed instructions can be found in the appendix
Mail:
support@fhgr.ch
Telefon (Notfall):
081 286 39 10 (intern 910)
Büro:
Gebäude A, 1.08
Öffnungszeiten:
Mo-Fr, 07:45 bis 11:30 Uhr
Mo-Do, 13:00 bis 16:00 Uhr (Am Freitagnachmittag bleibt der Support geschlossen.)

